Students in Break Through Tech’s CS 100 course learn about thwarting cyber attackers
Students in Break Through Tech’s CS 100 course learn about thwarting cyber attackers
The summer introductory CS 100 course being offered tuition-free as part of Break Through Tech Chicago allows students to discover computer science and envision themselves in a tech career. In the course’s third week, students focused on algorithms, data structures, ethics, privacy and security, and quantum computing.
Chris Kanich, an associate professor of computer science at UIC who conducts data-driven research on the socio-technical aspects of cybersecurity, shared insights on threat modeling. Students first developed their own inventories of their assets that they would like to protect: physical items, such as laptops, phones, and credit cards; their data, including emails and text messages; and their own personal security. Then they imagined a list of individuals who might threaten the security of those items, from cyber criminals and hackers to classmates and roommates. Finally, they suggested controls they could use to thwart attacks and protect their assets, including strong passwords, antivirus software, physical security systems, and turning off GPS location tracking on their devices.
Kanich advised: “You have to be aware of the attack surface, which is all of the things you can be attacked through to get at your assets, and your operational security, what you do on a day to day basis to protect yourself and others.”
He also led the class through an exercise in which they evaluated nine common approaches to minimize risk. He revealed that non-security experts valued behaviors such as antivirus software, only visiting known or familiar websites, and having strong passwords that are changed frequently and not shared with others. Conversely, security experts feel the most valuable controls are running software updates, employing two-factor authentication, choosing a strong, unique password, and utilizing a password manager.
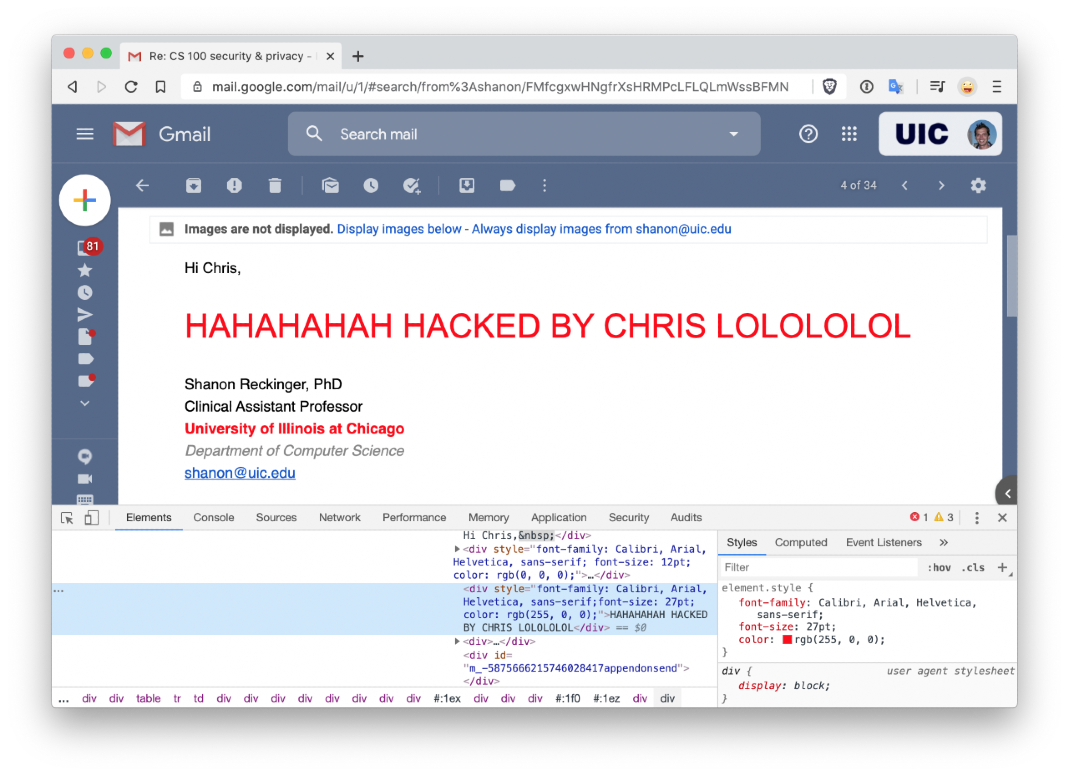
The lesson ended with students learning how to “be a hacker” by editing how existing webpages appeared on their own computers (the hack wouldn’t change the text on anyone else’s screen who was viewing the same web page).
“Every website has built-in web developer tools,” Kanich explained. “I own my computer, and I can manipulate what is shown on it.”